Though I haven’t been to the Ark Encounter exhibit in Williamstown, Kentucky, I did once visit the Creation Museum here in El Cajon. It was part of a field trip of sorts while at my undergrad, Point Loma Nazarene University in San Diego. I was there as a student reporter to document the PLNU science class’s visit. Students were scornful of the idea of the world being no more than 10,000 years old. At the time, I was still in that camp. But the mockery of the science students against the literalists, things like “I guess Jesus rode on a velociraptor,” was insulting to the believers.
A few years back, I was speaking to two friends and told them I didn’t know what to think about Genesis and the Flood. To them, saying I didn’t know was occasion for them to say they would pray for me.
This time, I was insulted.
But the question was about the inerrancy of the Bible story. I admit, I don’t know about many things in the Bible. But that issue opened a can of worms for other problems with a literal view. But the Flood story is such a major part of the Old Testament and the Bible as a whole, that the question of it as an actual event demands an answer.
So I am now thinking about the way the ancient Hebrews saw the Universe. This graphic from the University of Oregon’s Cosmology class can be found in various other versions.
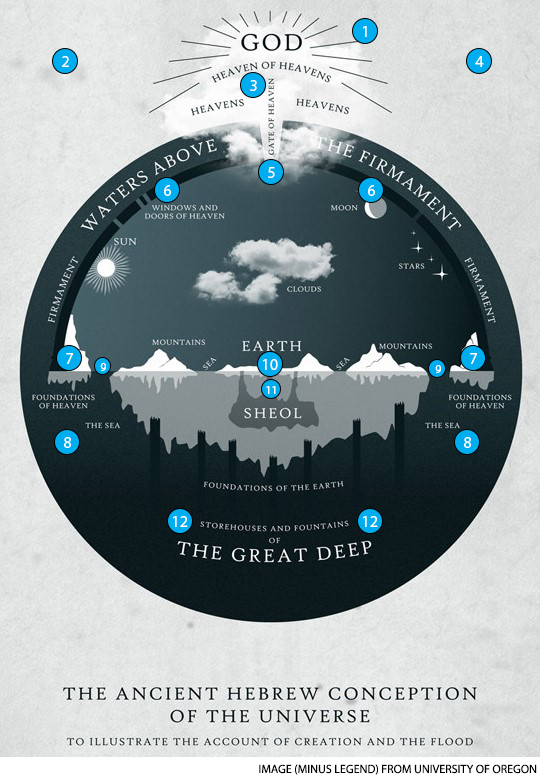
Looking at the graphic above, I believe the scientist view. When a new Earth creationist quotes those scriptures referencing “windows and doors of heaven,” “storehouses and fountains of the great deep,” “waters above the firmament,” “foundations of the deep,” “foundations of the Earth,” or “foundations of heaven,” they tend to think of it some form of poetry, but those lines reference the literal Hebrew cosmology.
The Flood was a local event. Not a worldwide cataclysm. The ark’s size finally works under that interpretation. I have no problem with Cain’s wife being a unrelated woman from a tribe not spoken of in the Bible; I no longer have to defend the idea that incest between Adam’s family was necessary for propagation of the species.
So, it doesn’t bother me if the Earth is 4.5 billion years old and the universe 14 billion. I want to talk more about literalism, a critical matter.
Continue reading “Hebrew Worldview in Scripture and Literalism, Pt. 1”

